Implementing Port Knocking on MikroTik Routers

In this post I will explain how to implement a powerful feature from MikoTik routers known as port knocking or "knock knock". Port knocking adds an extra layer of protection by allowing only authorized connections. By implementing this feature, you can improve the security of your network when opening ports to the internet.
Port knocking
Port knocking is a network security technique that involves sequentially connecting to a series of network ports in a particular order or pattern. The purpose of port knocking is to provide an additional layer of security by hiding open ports from potential attackers.
The main idea behind port knocking is that a potential attacker who does not know the correct port knocking sequence will be unable to discover or access the open ports on the target system.
Considerations
Port knocking should never be considered a replacement of encryption, and it does not provide an absolute guarantee of service security against potential attackers. When configuring a service for internet access, it is important to prioritize encryption and use robust passwords. Additionally, adopting a mindset of constant vigilance is crucial—always assume that you are under attack and remain proactive in implementing security measures to safeguard your system.
How to implement
First log in to your MikroTik router. For configuring the Port knocking I will use the terminal since it's faster and more easily to explain. You can use the WebFig if you want, it will be the same.
Once in the terminal navigate to "Firewall filter":
ip firewall filter
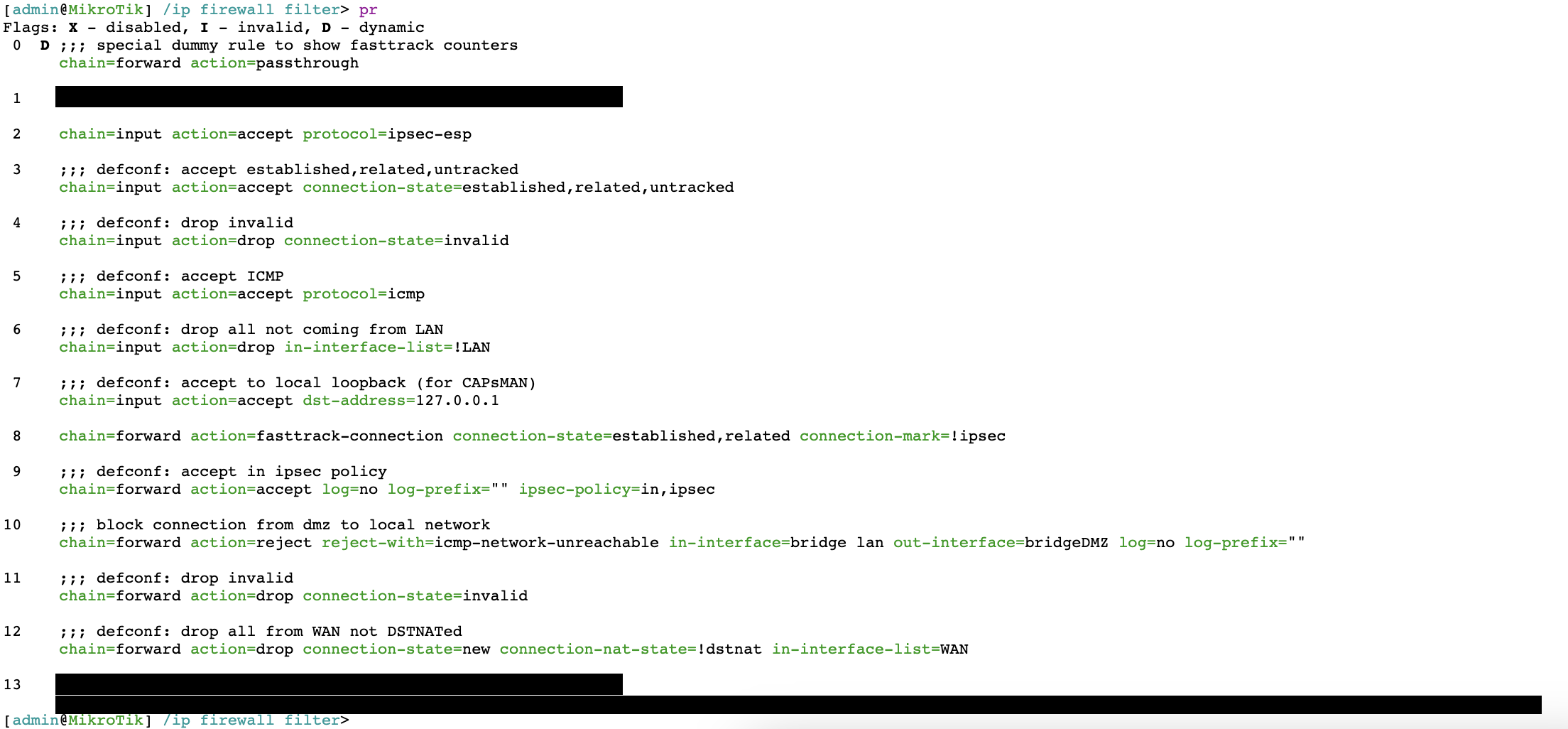
You can use the command "pr" for listing all the firewall filters:
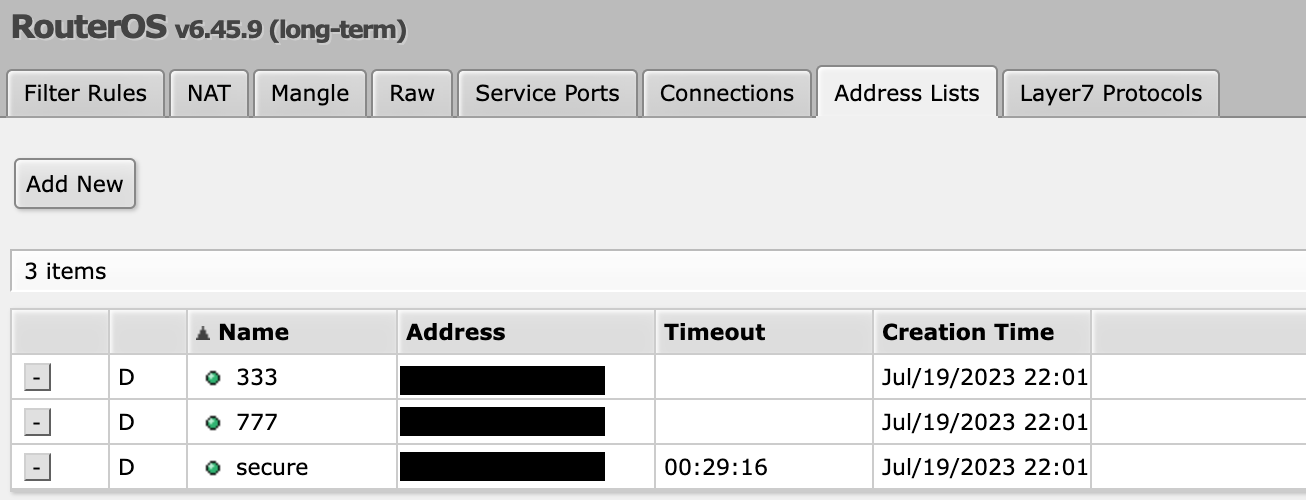
For my setup I will implement a total of three knock knock's. The ports will be:
First knock: 333
Second knock: 777
Third knock: 888
Create the first knock port. In this case, it will be port 333 and between the first knock and the seconds one must be in less than 30 seconds. Notice that we set this rule at the top of the list after the passthrough rule. For extra security, set the "in-interface-list" your WAN interface.
add chain=input action=add-src-to-address-list address-list=333 dst-port=333 protocol=tcp address-list-timeout=30s in-interface-list=WAN place-before=2
Now add the second knock in port 777 and 30 seconds of timeout. In "src-address-list" you must set the port of the first knock.
add chain=input action=add-src-to-address-list address-list=777 dst-port=777 protocol=tcp address-list-timeout=30s src-address-list=333 in-interface-list=WAN place-before=3
Finally, add the last knock in port 888. This knock will have a timeout of 30 minutes. This timeout will allow use to disconnect and connect again without need to repeat the knock sequence in a time frame of 30 minutes.
add chain=input action=add-src-to-address-list src-address-list=777 dst-port=888 address-list=secure protocol=tcp address-list-timeout=30m in-interface-list=WAN place-before=4
Add the following rule for users inside the secure list to have access to the router:
add chain=input action=accept in-interface=WAN src-address-list=secured place-before=5
Now the port knocking is configured and ready to go!
You must have the following filters:

Prevent Knock Knock from Nmap scanning
Using an Nmap scan, it is possible to perform a Knock Knock scan on all ports and potentially gain access to secured ones. Nmap operates by detecting open ports, and although it discovers ports in a seemingly random order, there exists a possibility that it stumbles upon the correct sequence.
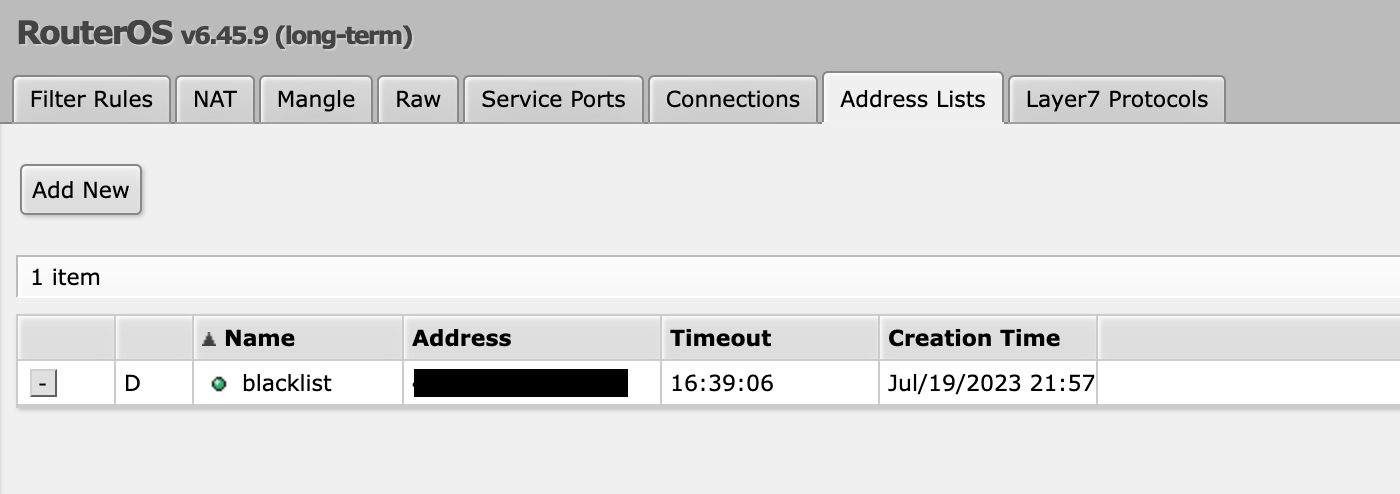
In order to prevent this we will use a blacklist. First, we are going to create a rule to block everything inside the blacklist.
add chain=input action=drop in-interface-list=WAN src-address-list=blacklist place-before=1
Create a rule that if someone scans the port 666 it will be blocked 1000 minutes:
add chain=input action=add-src-to-address-list protocol=tcp address-list=blacklist address-list-timeout=1000m in-interface-list=WAN dst-port=666 place-befor
e=1
So now, if someone execute a Nmap command it will scan port 666 and we will block the connection.
But, if we instead execute the following command we will have access to the router:
for x in 333,777,888; do nmap -p $x -Pn storm.ddns.net; done